There’s an old joke circulating out there that occasionally crops up in people’s inboxes:
You have just received the [Amish/Polish/Aggie, etc.] Virus! Because we don't know how to program computers, this virus works on the honor system. Please delete all the files from your hard drive and manually forward this virus to everyone on your mailing list. Thanks for your cooperation.
It goes without saying that this would be a Bad Idea. That said, there is a very current scam going on which I ran across yesterday, in which the victim is carefully walked step-by-step through the operations necessary to allow Bad Guys to take control of their computer. I referred to it in a previous post, but here’s the complete run-down.
While researching spoofed and phishing URLs, I decided to use a misspelling of a popular website as an example. I typed in http://www.micorsoft.com (DO NOT DO THIS!) and discovered a rat’s nest of scam operations embedded in this one redirect.
According to WHOIS, the domain is registered thusly:
Domain Name: MICORSOFT.COM
Registrar: EPIK, INC.
Whois Server: whois.epik.com
Referral URL: http://epik.com
Name Server: NS1.DNSLINK.COM
Name Server: NS2.DNSLINK.COM
Status: ok
Updated Date: 19-oct-2014
Creation Date: 13-oct-2001
Expiration Date: 13-oct-2015
Epik is a domain-name registry service, so beyond that I don’t have the chops to dig deeper and see who is really running this operation, but this much I know – they’re wastes of human cytoplasm.
This domain redirects to a number of different scams.
1) You’ve won a prize!
Here’s the first popup. The URL is your typical scam alphabet soup address.
After answering four inane questions about age, whether you shop on line, gender, etc. you’re presented with this:
Well, of course I qualify. You think the scammers would turn down a sucker? No, I didn’t win a prize, I won a “chance” for a grocery gift card. Call the number, and what you hear is “Congratulations! Won a chance to win a gift card!. Stay on the line to complete your entry! Dingdingding your initial entry has been registered, but stay on the line for other additional offers!” You then are bombarded with advertising. Since I used Google Voice to call, there’s no way they could possibly know who is calling or how to contact you if you were really a winner – this is just spamvertising, pure and simple.
2) The Random Cybersquatting Page
Next, i was redirected to this horrific URL:
http://www.searchnet.com/Search/Index? utm_source=8&utm_campaign=AuctionErrorWithInfo&utm_term=XP%20Home%20Premium; Microsoft;microsoft;download%20internet%20explorer%2010;microsoft.com;www.microsoft.com; microsoft%20windows;window%20live%20messenger;servers%20xp;microsoft%20help%20support; microsoft;microsoft%20help%20center;online%20ms%20training; microsoft%20programs;xp%20small%20business%20edition%20;downloads; microsoft.com;windows%20updates&utm_medium=Ciclostare32
User Nokkenbuer at WOT (Web of Trust) posted on 09/21/2014:
- I don’t trust
- Malware or viruses
- Poor customer experience
- Scam
- Misleading claims or unethical
- Privacy risks
- Suspicious
- Spam
- Potentially unwanted programs
This website was involved in redirecting me to a malicious site after accessing a typosquatter website (http://www.micorsoft.com/). I do not trust it and may aid in infecting your computer with unwanted malware, spyware, or grayware.”
By the way, if you don’t have the WOT extension on your computer, I’d recommend it. It gives you advance warning of sites that have been flagged as malicious, like this:
For any site, you can always “read more” to see what users have said. It’s wise to do, because on occasion a website was flagged early for suspicious behavior, but domains change hands and it could be a legitimate site at the present time. User comments will usually reflect this. At all events, you have the option of leaving before you actually visit a potentially dangerous website. Sign up, and you can leave your own feedback for websites as well.
3) Is Your Computer Running Slowly?
If you click OK, you’re directed to this page:
This one looks slick and official, but it’s a solid guarantee that if you call that toll-free number, you’re at risk for being scammed or having your computer infected or both.
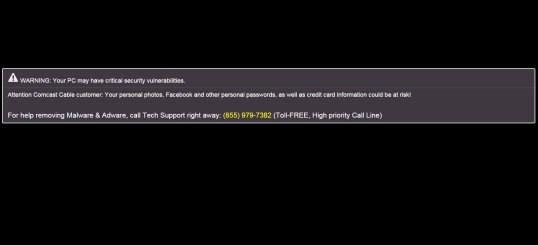
4) The Scare Tactic
This is the one I referred to in my earlier post, and today I followed up on the game to see how it plays out.
This page is a little different than the first one I encountered; it doesn’t mention specific viruses, but includes an annoying, repeating, and loud chirp to add urgency to the scam. If you try to navigate away from the page, you get this:
If you bite and call the number (855- 979-7382) you will be connected to a polite-sounding Indian or Pakistani boiler-room worker who will engage you as follows:
- I was asked kind of problems you are experiencing, what kind of computer I am running, and what my operating system is.
- On a Win7 box (your mileage may vary for other operating systems) I was asked to hit “Windows-R” to open the Run dialog, and then type in “MSConfig” and hit enter. This is harmless, but displays running services on your computer.
- I was asked if more than 15 services were stopped?
- I responded that yes, more than 15 services were stopped.
- The agent informed me that since more than 20% of my services were stopped, my system was vulnerable to application errors. Once Windows 7 has services stopped, that is the main problem. This, of course, is utter bulldust, but is technobabble enough to flummox most callers who get this far.
- I was told that we need to check why these services are stopped. Again directed to the “Run” dialog, I was instructed to type in “hh h” and hit “Enter”. This brings up the HTML Help Window, which “Cannot be Displayed.”

- I was instructed to hover my mouse over the little question-mark icon in the window, and select the “Jump to URL” option.

- I am presented with a dialog box, and asked to enter the specified URL:

Note: This is a sneaky way to get you to visit a website, instead of typing it directly in the URL bar. - Once this is done, I am directed to this website: https://secure.logmeinrescue.com/customer/code.aspx

This is a website which allows outside users to take control of your computer, usually for tech support reasons. If you trust the party on the other end it can be useful, although I prefer to use TeamViewer. - Before proceeding, the agent had me run inetcpl.cpl, click on the connections tab, and ensure that no proxy was being used.
- Having done this, the agent instructed me to enter the code 941073, and hit “Enter.” He asked me what I saw on my screen.
- At this point, I told him the only thing I saw was myself closing Chrome, because I had no intention to give control of my machine to a bunch of scammers, and hung up.
There are enough methods out there that the Bad Guys can infect your computer if you’re not careful, but helping them with the process is generally a Lousy Idea.
Be careful out there.
The Old Wolf has spoken.







Pingback: Scam: The Blue Screen of Death | Playing in the World Game
Hi , my gilrfriend unknowingly fell for the last scam you laid out for us.. She gave someone access to her laptop apparently for upwards of an hour and then paid the nice Indian sounding fellow 150 dollars for some “anti malware programs” .. He installed and ran cc cleaner which is free obviously, then installed malwarebytes anti exploit, but the last program that made me particularly nervous was one called global corp, that immediately disappeared from the computer after installing it which I found weird. Long story short, we need help resolving this situation..any advice?? Im calling Dell in the meantime to see if they have any ideas. Thank you
Yarg. Sorry that happened. You are wise and cautious to be worried. Without knowing, my suspicion is that the “vanished” program is now operating in the background, having turned your ladyfriend’s computer into part of a botnet, or else it’s scanning her drive for passwords and financial data. It’s hard to tell with these people. I did a search for “global corp” malware and came up poor.
Without knowing the exact chain of events that got your g/f on the phone with this friendly agent, it’s hard to know exactly what went down, but it sounds fishy. There is an outside chance that everything he did was legit (although possibly useless), but the fact that the program vanished is highly suspicious.
Malwarebytes Anti Exploit is a package that protects existing anti-malware packages from being hacked by zero-day exploits. Along with calling Dell, I would (by yourself) make sure you have Malwarebytes Anti Malware package installed, or Kaspersky, or some other reputable virus checker, and run it. CC cleaner is a registry cleaner which would not protect against viruses and can be helpful or can cause problems.
Good luck.
Pingback: Beware the Zeus virus (No, you’re not infected) | Playing in the World Game