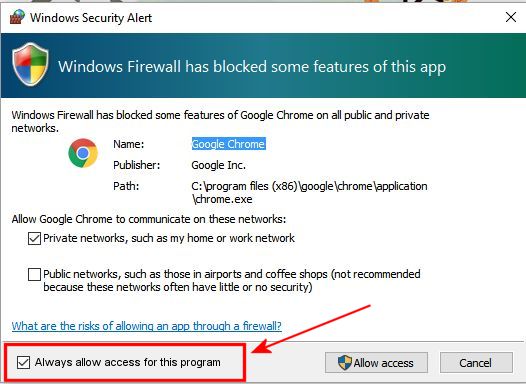
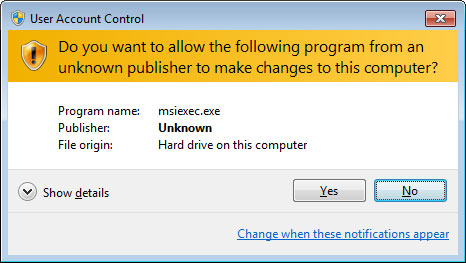
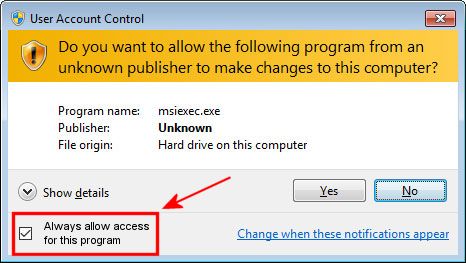
In my previous post, I ranted a bit about Microsoft’s efforts to alienate their customers by making competing or foreign programs (like Chrome – horrors!) incompatible or forcing them to ask permission to run, every time. We’re talking Windows 10 here, the latest and greatest.
Here’s an old joke, but one which remains totally valid in the 21st century:
A helicopter was flying around above Seattle when an electrical malfunction disabled all of the aircraft’s electronic navigation and communications equipment. Due to the clouds and haze, the pilot could not determine the helicopter’s position and course to fly to the airport. The pilot saw a tall building, flew toward it, circled, drew a handwritten sign, and held it in the helicopter’s window. The pilot’s sign said “WHERE AM I?” in large letters. People in the tall building quickly responded to the aircraft, drew a large sign and held it in a building window. Their sign read: “YOU ARE IN A HELICOPTER.” The pilot smiled, waved, looked at her map, determined the course to steer to SEATAC airport, and landed safely. After they were on the ground, the co-pilot asked the pilot how the “YOU ARE IN A HELICOPTER” sign helped determine their position. The pilot responded “I knew that had to be the Microsoft building because, like their technical support, online help and product documentation, the response they gave me was technically correct, but completely useless.”
One would think that after all these years as the 900-lb gorilla in the software space, someone at Microsoft would wake up and realize that this is a critical failing that generates massive ill will toward the company.
No, I’m not blowing smoke. Here’s an example, related to my last post.
I went to the Microsoft support site today, and asked a simple question: “Why does Windows Firewall in Win10 block Google Chrome?”
Here’s the page that comes up – one relevant to Windows Vista, dated 2011.
Someone named “Samuthra G,” tagged as a Microsoft agent, replied:
Hi,As the issue is with Google Chrome I would suggest you to post your query in the Google forum for better assistance:
http://www.google.com/support/forum/p/Chrome
And this was designated as the “most helpful” response. Thank you so much, Microsoft and Samuthra G; nothing like blowing an unhappy customer’s problem off by blaming someone else.
Two months later, a user named “Karmana” followed up with the perfect response:
Why is it, over the years, that I have noticed the vast majority of supposed Windows or Microsoft higher-certified helpers cannot seem to actually read the questions asked by the original poster? Samhrutha, your answer to QW_895 is not only unhelpful, but if you were/are a Microsoft employee, then it is also highly irresponsible to blow off the OP by saying, “It’s not our problem.” Taking responsibility for one’s own products is a strong first step in positive Public Relations!
To this day, this is my boilerplate experience with Microsoft forums. First of all, the people who answer never give a relevant answer – it probably has to do with the fact that their first language is not English, and that they’re paid pennies per hour to respond to these questions. Second, if they do give a response that’s even on-topic, it’s almost always so technical as to be incomprehensible or un-implementable by the average user.
Today I tried contacting the Microsoft support site, just to see what happens:
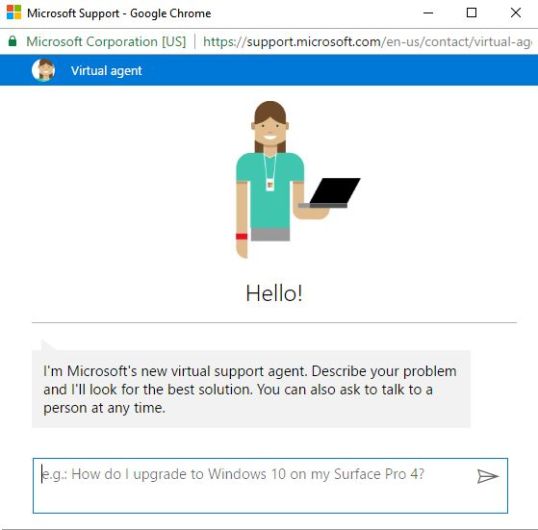
Having already tried a search without success, I figured I’d take advantage of their offer:
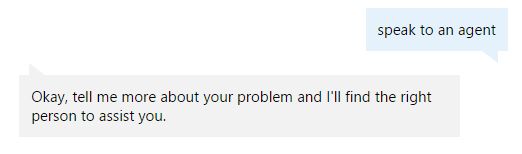
So I entered my question again: “Why does Win10 firewall block Chrome?” What I got was a list of articles – and once again, the most relevant hit is the worthless exchange I referred to above.
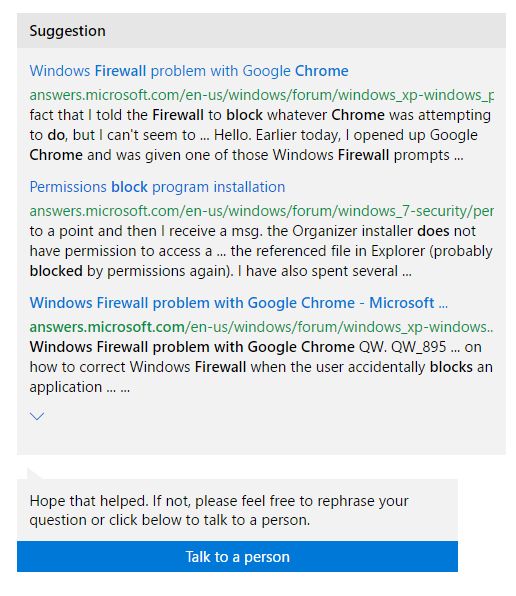
So I clicked the “Talk to a person” link, and was connected via Chat to a friendly Microsoft agent somewhere on the other side of the world.
“Clarisse” asked me some questions about which version of Windows I was using, provided a case number, and ended up suggesting that I uninstall and reinstall Chrome. So just for the hell of it, I gave that a try – predictably, without success. These agents in India or wherever are minimally trained, minimally paid, and working from scripts without much understanding of what’s happening under the hood.
If I wanted, I could pay $149.00 per year for premium Microsoft support, which would allow me to ask questions at any time and also enable remote desktop support, but I somehow feel that paying for support to solve problems that Microsoft generates is probably not the best allocation of my resources.
The challenge is that Microsoft is so widely accepted as the de-facto standard in the business world that people need it to conduct their daily affairs, and most people would rather muddle along with the best they can do rather than delve down into the guts of an operating system to try to find a fix or a workaround. Microsoft knows this, and based on results, they don’t care to spend any time, effort, or money to improve their byzantine and useless support system.
It’s sad. For myself, I don’t really feel like facing the Linux learning curve, and I’m seriously afraid of something like this:

As for Apple, I love the idea of the Macintosh platform, but unless the company brings their prices in line with PC hardware, I won’t be able to justify the expense. From a functionality standpoint, the lines between PC and Mac world have blurred considerably since 1984 when the Mac was introduced as the sexy computer for the rest of us, so the draw has diminished substantially.
Still not a happy camper.
The Old Wolf has spoken.