(Thanks to Techsrus for the image)
My cubicle neighbor (at the job we just both got laid off from yesterday, but that’s another story) showed me a couple of emails he had gotten in his Gmail account – each sported the header “Notice to Appear in Court.” I told him they were probably scam threat letters and hoping to extort money.
I got one myself today, and decided to explore it a little further.
—————-
|
Notice to appear in court,
Hereby you are notified that you have been scheduled to appear for your hearing that will take place in the court of Detroit in April 03, 2014 at 11:30 am.You are kindly asked to prepare and bring the documents relating to the case to court on the specified date.The copy of the court notice is attached to this letter. Please, read it thoroughly.Note: The case may be heard by the judge in your absence if you do not come.Yours very truly,
SAMPSON Hays
Clerk of court
Win32/Kuluoz is a trojan that tries to steal passwords that are stored in certain applications and sensitive files from your PC. This trojan could also download other malware to your PC, like other variants of Win32/Kuluoz and Win32/Sirefef, and variants of rogue security software likeWin32/FakeSysdef and Win32/Winwebsec. This threat tries to hack your email accounts and file transfer programs.
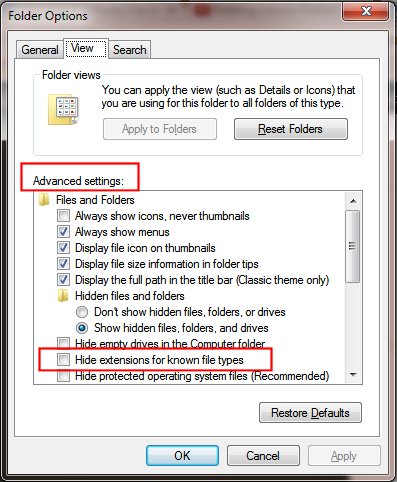
1. Always display file extensions. This option is turned off by default by Microsoft on its newer operating systems, which in my opinion is a dangerous and foolhardy idea. This means that instead of seeing “Notice_to_Appear_TY4769.zip” and “Court Notice.exe”, you would only see “Notice_to_Appear_TY4769” and “Court Notice.” To fix this, follow the procedure below for your operating system:
To show or hide file name extensions (Windows 7)
-
Open Folder Options by clicking the Start button
 , clicking Control Panel, clicking Appearance and Personalization, and then clicking Folder Options.
, clicking Control Panel, clicking Appearance and Personalization, and then clicking Folder Options. -
Click the View tab, and then, under Advanced settings, do one of the following:
-
To show file name extensions, clear the Hide extensions for known file types check box, and then click OK.
-
To hide file name extensions, select the Hide extensions for known file types check box, and then click OK.
-
To show or hide file name extensions (Windows 8)
- Open Windows Explorer and go to “View” and then click the Options button > Change folder and search options
- Scroll to “Hide extensions for file types is known”
- Uncheck it and click OK.
To show or hide file name extensions (Windows XP)
- Double Click on My Computer.
- Click on Tools > Folder Options… in the menus.
- Click on the View tab.
- Remove the check from Hide extensions for known file types.
- Click the OK button.
2) Make sure you have robust malware detection software installed. AVG Free, Microsoft Security Essentials, and Kaspersky are all good options. The first two are free, the third reasonably priced and somewhat more robust than the other two.
3) ☞ NEVER ☜ open attachments from unknown senders, especially a file that contains “.exe” anywhere in its name.
(Did I make that emphatic enough? I’d make it blink if I could.)
A lot of folks are savvy enough to spot this as a scam in an instant, but this particular email is official-looking enough to scare a lot of vulnerable computer users; the scammers don’t care if you actually appear anywhere – they just want you to open that never-to-be-sufficiently-damned attachment. If you are technically savvy and you have loved ones, either elderly or otherwise vulnerable, watch out for them. Educate them. You don’t want them becoming victims of scams or nefarious behavior like botnets.
This has been an Old Wolf public service announcement.