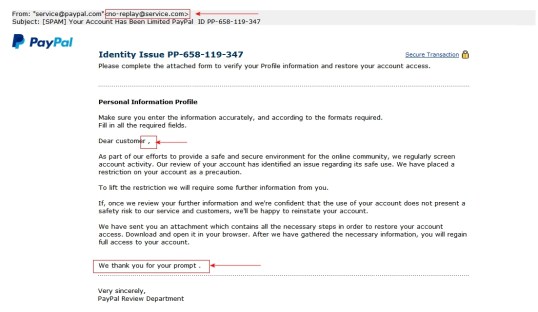
Here’s the email that came to me yesterday:
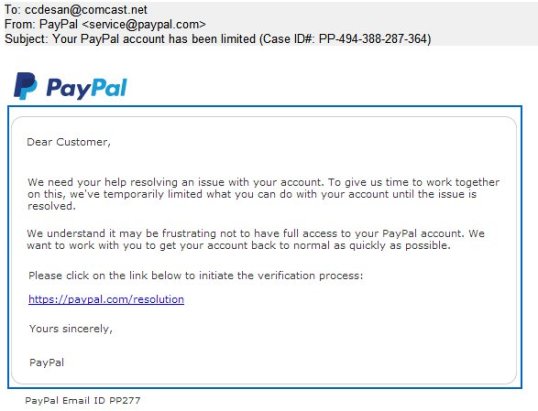
- Notice that it appears to come from “Paypal.com,” However, the original sender was
- Second, the message is an image rather than text. That’s a red flag right there. The images link back to:
These are definitely nothing linked to PayPal. So we know even without any further examination that we are dealing with a phishing scam.
The image itself, if you click on it, will lead you to a long URL which actually contains the email address that their phishing email was sent to. If you click on these links, they know who you are.
http://redirect.paypal.com.0.session…..=MyEmailAddress@comcast.net
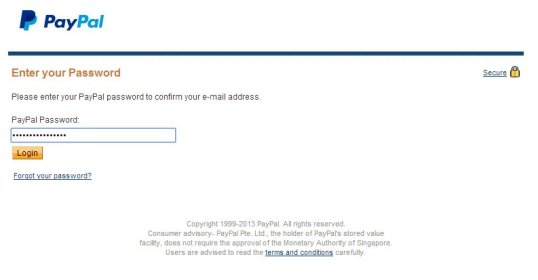
So notice that when you get to the phishing website, they already have your email address. This is what makes the scam more credible – they’re not asking for your PayPal ID, because they are counting on the fact that you use your same email address as your PayPal address, and they already have that.
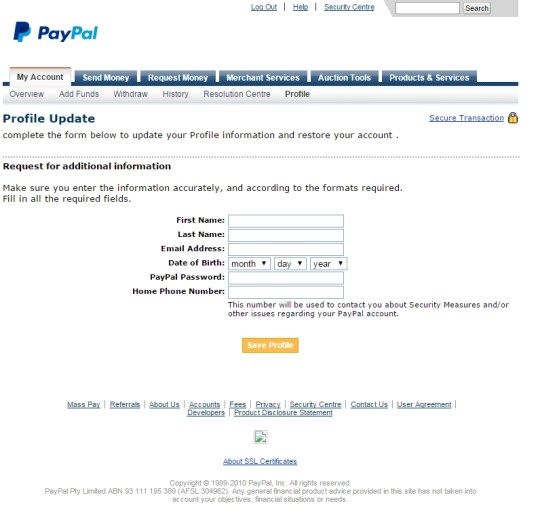
If you foolishly enter your password, the first thing you’ll see is this bit of misdirection:
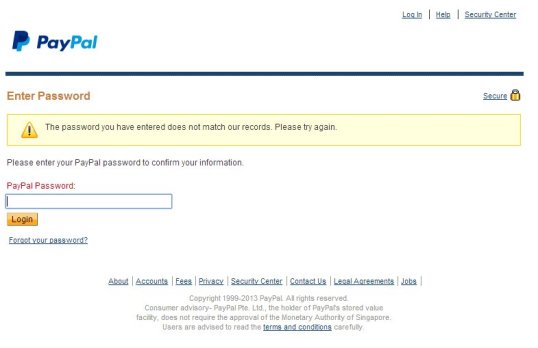
But that’s just a clever bit of misdirection. So you try again, and this is what you get next:
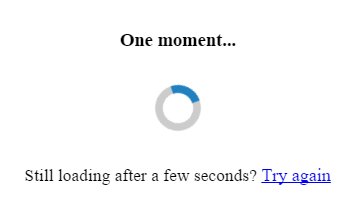
Which soon passes to:
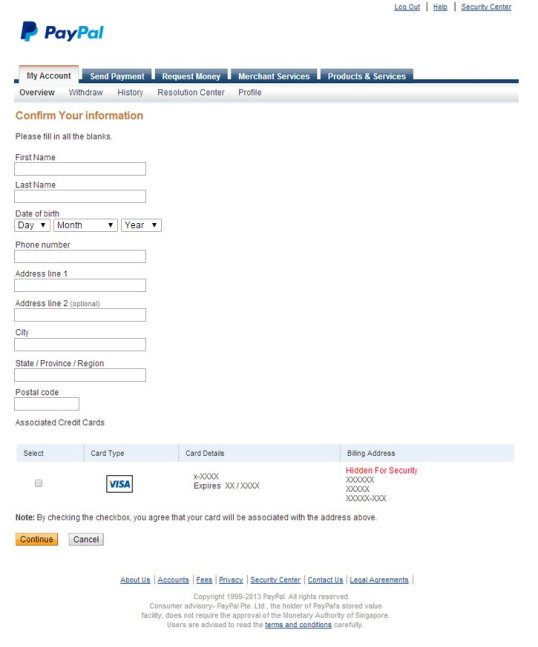
And off to the races we go.
REMEMBER: Banks or PayPal or other financial institutions will NEVER ask you to verify information like this via email. All such requests are SCAMS.
When I check out websites like this (don’t try this at home – you could also be picking up a lot of malware if you’re not properly protected), I usually enter really insulting phrases for names, cities, and so forth. It’s a small thing, but it’s really the only way I can get under the skins of these criminals.
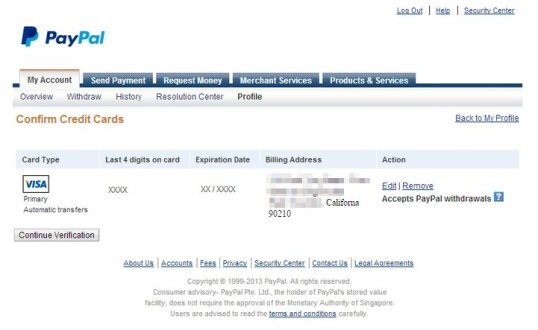
That billing address is nothing I would ever want to repeat in polite company – but notice that the scammers are trying to make their victim think they already have a credit card on file, and you’re just supposed to verify it.
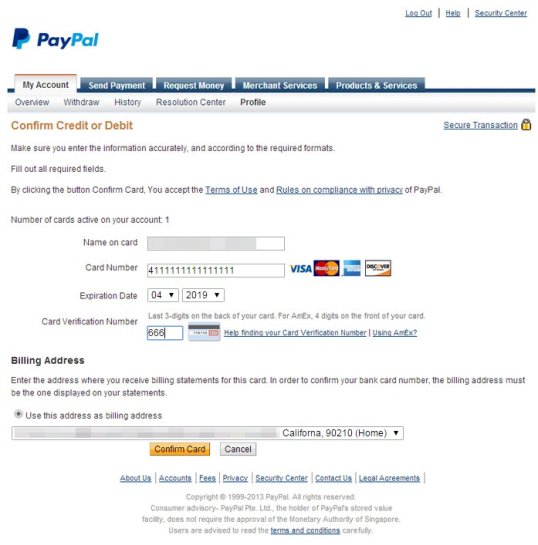
So again I give them some bogus information that could never be used as a real card or be used to hurt anyone else.
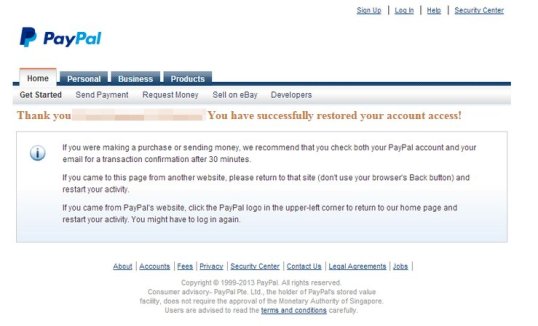
The last screen will redirect the victim, once they have handed over their sensitive information to thieves, to the real PayPal website. Notice however – nothing else on the page works. All the other links are non-existent.
This scam is well-contrived enough that I fear any number of people will be taken in.
The most important thing to remember is that, as I said before, PayPal will NEVER ask you to give up sensitive financial information like this through an email message.
Be careful out there, and protect your loved ones.
The Old Wolf has spoken.